On March 4, cybersecurity firm, Palo Alto Networks discovered that the OS X installer for version 2.90 of the BitTorrent client Transmission was infected with ransomware, just a few hours after installers were initially posted.
The ransomware has been named “KeRanger.” KeRanger, which appears to be the first fully functional ransomware seen on the OS X platform.
The KeRanger application was apparently signed with a valid Mac app development certificate so it was able to bypass Apple’s Gatekeeper protection.
OS X Malware – How It Works
If a user installs the infected apps, an embedded executable file is run on the system. KeRanger then waits for three days before connecting with command and control (C2) servers over the Tor anonymizer network. The malware then begins encrypting certain types of document and data files on the system. After completing the encryption process, KeRanger demands that victims pay one bitcoin (about $400) to a specific address to retrieve their files. It also appears that the malware is also attempting to encrypt Time Machine backup files to prevent victims from recovering their back-up data.
Transmission posted this warning on their web site:
Read Immediately!!!!
Everyone running 2.90 on OS X should immediately upgrade to and run 2.92, as they may have downloaded a malware-infected file. This new version will make sure that the “OSX.KeRanger.A” ransomware (more information available here) is correctly removed from your computer. Users of 2.91 should also immediately upgrade to and run 2.92. Even though 2.91 was never infected, it did not automatically remove the malware-infected file.
Transmission 2.92
In addition, the Transmission application is presenting this update notice:
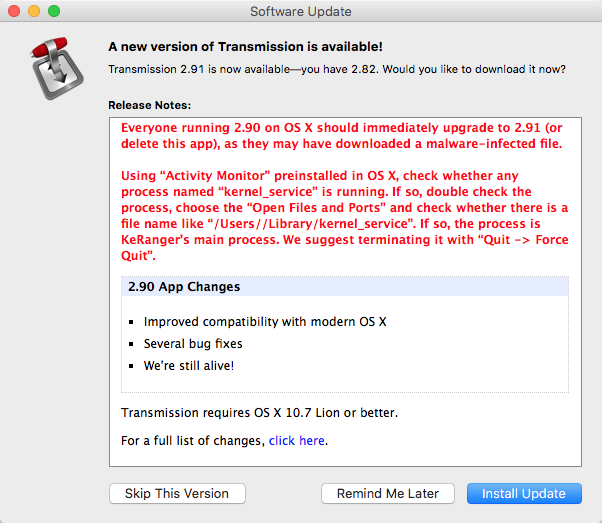
Transmission Update Notice
Apple has revoked the abused certificate and has updated XProtect signatures. If a user tries to open a known infected version of Transmission, a warning dialog will be shown that states “Transmission.app will damage your computer. You should move it to the Trash.” Or “Transmission can’t be opened. You should eject the disk image.” In any case if you see these warnings, we suggest to follow Apple’s instruction to avoid being affected.
How To See If You Are Infected.
It appears the malicious installer files were available for download from the Transmission site between 11:00am PST, March 4, 2016 and before 7:00pm PST, March 5, 2016.
Palo Alto Networks has the following suggestions to check your system:
- Using either Terminal or Finder, check whether /Applications/Transmission.app/Contents/Resources/ General.rtf or /Volumes/Transmission/Transmission.app/Contents/Resources/ General.rtf exist. If any of these exist, the Transmission application is infected and we suggest deleting this version of Transmission.
- Using “Activity Monitor” preinstalled in OS X, check whether any process named “kernel_service” is running. If so, double check the process, choose the “Open Files and Ports” and check whether there is a file name like “/Users/<username>/Library/kernel_service”. If so, the process is KeRanger’s main process. We suggest terminating it with “Quit -> Force Quit”.
- After these steps, we also recommend users check whether the files “.kernel_pid”, “.kernel_time”, “.kernel_complete” or “kernel_service” existing in ~/Library directory. If so, you should delete them.
Information for this story was taken from and more details are available from Palo Alto Networks website.
If you liked this article, please consider sharing it with your friends and leaving a comment below.
Also, don’t forget to “Like” us on Facebook and “Follow Us” on Twitter.



Leave a Comment
You must be logged in to post a comment.